Privilege Access Management
Who are these privileged users ?
Privileged users are most of the time IT and Network administrators like windows admin, linux admins, database admins, network admins.
These users have broad access to IT infrastructure to perform essential duties like configuration changes, system maintenance, backup/restore that ordinary users/employees are not authorized to perform.
Most of the time these privileged users use “non-personal” and “super-user or power-user” accounts like root account, administrator account, sysdb account.
Privileged users are not limited to IT and network admins, but also users as follow:
- Help desk agents have restricted access but to a broad range of assets.
- Help desk agents have restricted access but to a broad range of assets.
- Business Application (e.g. ERM, Salesforce) users or users of an organization’s social media (e.g. LinkedIn, twitter) accounts.
- Nonemployees such as vendor support, consultants, contractors.
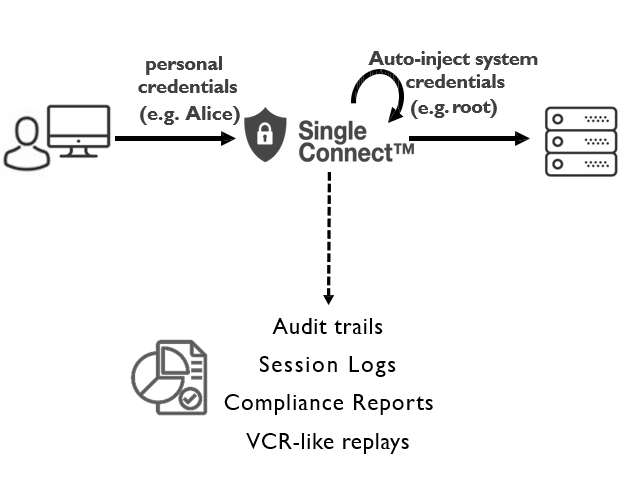
Privileged Access Management represents the set of critical cybersecurity controls that address the security risks associated with privileged users and privileged access in an organization.
Privileged accounts (e.g. root, administrator) provide elevated, often unrestricted access to an organization’s underlying information systems and technology, making them rich targets for both external and internal malicious actors. Often referred to as “the keys to the kingdom,” these accounts have been used in successful attacks to gain access to corporate resources and critical systems (e.g. “crown jewels”), resulting in data breaches. As a result of this elevated access and capability, privileged accounts must be carefully controlled and monitored.
PAM is a domain within identity and access management that focuses on monitoring and controlling administrative accounts/users within an organization. Many organizations use PAM systems to provide oversight of these powerful accounts. By implementing a PAM system, organizations are able to protect, monitor, and audit privileged account access, which in turn can reduce the possibility of data destruction, data exfiltration, and system failure.
Single-Connect PAM Benefit:
- Control access to, and the use of, privileged accounts (both on-premises and in the cloud)
- Manage and monitor the activity of privileged accounts.
- Audit the activity of privileged accounts.
- Receive alerts or notifications when privileged accounts are used for unauthorized or out-of policy activities.
- Encourage personal accountability among the users of privileged accounts.
- Enforce stringent policies for “least privilege” and separation of duties.
Go to Krontech Single-Connect PAM provider https://www.krontech.com/